TorBroker - Security vulnerability found
Anyone who run a tor exit node can change this JavaScript and make some bad things:
The above link is actually linking to Google (ajax.googleapis.com):
and not to
as you may think.
Loading a JavaScript thought an insecure tor exit node can be very dangerous.
One hour after report I received an answer from the TorBroker:
I confirm that this problem is solved:
<!--[if lt IE 9]>
<script src="http://html5shim.googlecode.com/svn/trunk/html5.js"></script>
<![endif]-->
<script src="//ajax.googleapis.com/ajax/libs/jquery/1.8.1/jquery.min.js"></script>
The above link is actually linking to Google (ajax.googleapis.com):
http://ajax.googleapis.com/ajax/libs/jquery/1.8.1/jquery.min.js
and not to
http://torbrokerge7zxgq.onion//ajax.googleapis.com/ajax/libs/jquery/1.8.1/jquery.min.js
as you may think.
Loading a JavaScript thought an insecure tor exit node can be very dangerous.
One hour after report I received an answer from the TorBroker:
To exploit this vulnerability an attacker would have to control the specific exit node the targeted TorBroker user is currently exiting through. This is not easy to accomplish, so we do not consider this to be a critical vulnerability. However, given the nature of our service we insist on providing the best possible security for our customers, so we have updated the code to remove this point of attack.
Thank you for the report!TorBroker
I confirm that this problem is solved:








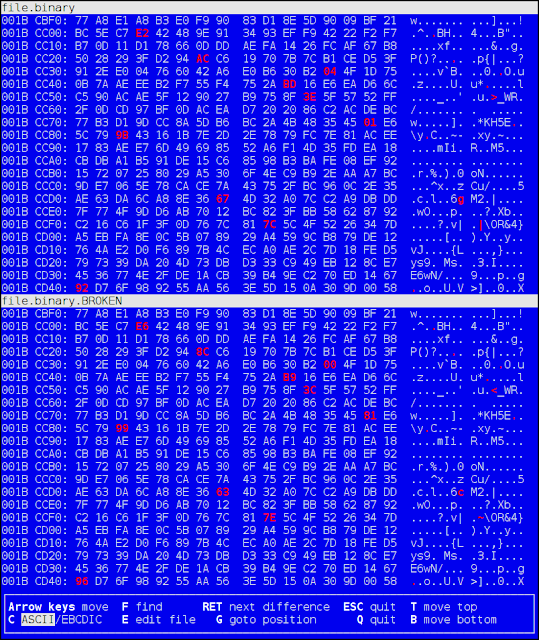
its a hidden service (.onion) there are no exit nodes.
ReplyDeleteThere should be no exit nodes involved at all... but there are - the site was embedding objects from non-onion urls.
Delete